
5 Barriers to CMMC Compliance
March 15, 2023

Webinar OVERVIEW:
CMMC compliance can be challenging for many DoD contractors. Even the most security-conscious companies find some DoD security requirements confusing, which can prevent contractors from passing their C3PAO assessments.
As a registered C3PAO candidate that has worked with more than 100 companies over the last five years on CMMC and NIST SP 800-171 compliance, InfoDefense has identified five CMMC "gotchas" that cause the most confusion.
Join InfoDefense for a live webinar to learn about the most common CMMC misconceptions, how to avoid these unnecessary delays, and understand how best to address these "5 Barriers to CMMC Compliance:"
Speakers:

Kevin Wheeler
Managing Director & Founder, InfoDefense
WEBINAR TRANSCRIPT:
I wanted to thank everyone for joining us today to talk about the “5 Barriers to CMMC Compliance.” This is a topic that has been very top of mind for Kevin and InfoDefense here for a number of years. Finding that many companies that they've worked with for compliance over the years face a handful of challenges that are very similar, whether it's misconceptions that they thought a specific requirement or regulation needed to be handled a certain way or whether it was just an oversight in terms of not thinking why they needed to handle a security control another direction. This is where InfoDefense found that there's a number of things that have caused organizations to potentially get delayed in implementing CMMC or run into an obstacle that sets them back in terms of raising their SPRS scores moving forward.
So, without further ado, it's my honor to introduce Kevin Wheeler, who for the last 20 years has been the Founder and Managing Director of InfoDefense, which is a managed security service provider specializing in helping small and medium DoD contractors achieve and maintain CMMC compliance. His firm is a registered C3PAO candidate with the CMMC Accreditation Body. And the firm has worked with more than 100 companies over the last five years on CMMC and NIST SP 800-171 compliance. Kevin personally has more than 25 years of information security, IT audit and compliance expertise. He actively serves on the Advisory Council of the C3PAO stakeholder forum as one of 11 members on its board of directors nationwide, so you're in good hands. He's also the author of three editions of a book on “IT Auditing,” and has a background previously with Bank of America, where he was responsible for network authentication encryption technologies, as well as an enterprise security strategist at Symantec.
So, I'm gonna let Kevin jump in and take over the presentation to help everyone understand the “5 Barriers to CMMC Compliance” that most defense contractors face.
The Five Barriers to CMMC Compliance:
Thanks, Scott. So we want to start by talking about why we're doing this series. This is the second webinar in a series that we're putting together. The reason why we're doing this is because there is a tremendous amount of misinformation about CMMC, lots of different things. A lot of the people we talked to say you hear different things in different places. And I really want to provide some clarity, at least as much as possible right now.
Now, bear in mind, DOD is still in rulemaking. CMMC is currently not a mandate. It will be more than likely towards the end of this year. It could be into 2024. And we'll talk about that in a minute. But what we're seeing is a lot of organizations are kind of waiting right now, to see what happens. And we are really advising organizations to go ahead and start their preparation and move towards CMMC compliance. It's great that you all are here, because you're learning about some of the pitfalls and some of the things we see continuously with CMMC compliance.
Why is CMMC so Important?
So let me go ahead and start by talking about why CMMC is so incredibly important. So for any of you who weren't on the last webinar, we had a different slide. And going forward, we're gonna just use different warfighting equipment, and just compare the US version to the Chinese version. And what you're gonna see is this has a lot of similarities. And the reason why there's a lot of similarities in these two planes, in this case, the F-35. And the FC-31 is because of the fact that they're using a lot of the same technology. It's stolen technology. And the way that this technology is acquired is sometimes big breaches. But often times, it's just small things here and there that would be considered Controlled Unclassified Information that are aggregated and might be just the specifications for a part on the plane, for example. They're aggregated so that they can build the entire aircraft in this case. So the reason why we're doing CMMC is really foreign national security.
CMMC Facts:
So a few facts about CMMC. Originally, it was released in 2020. It's the next version of DFARS 252.204-7012. And what the big difference is, in the initial version there were some additional requirements. Now they've switched to CMMC 2.0. The biggest difference is the fact that there's a third-party certification. So the requirements that have been in place since 2017, with NIST SP 800-171 are still the same differences. It's since they were not necessarily being followed uniformly, that DOD has decided to go out and use third-party certifications. And that's specifically for companies that have Controlled Unclassified Information (CUI). There's also CMMC Level 1, which is for Federal Contract Information (FCI), and we'll be focusing on Level 2, which is CUI, during this presentation.
DON't Wait to preparE:
So a couple of things in relation to timing. On CMMC, we could see CMMC certification being a requirement for new contracts and new task orders starting as early as later this year. More than likely, it'll start in 2024. The DoD is still telling us that they are going to add the CMMC requirements to all contracts by Fiscal Year 2025. Now, there's been some delays and we don't know if that's going to hold. But that's what they're still saying today.
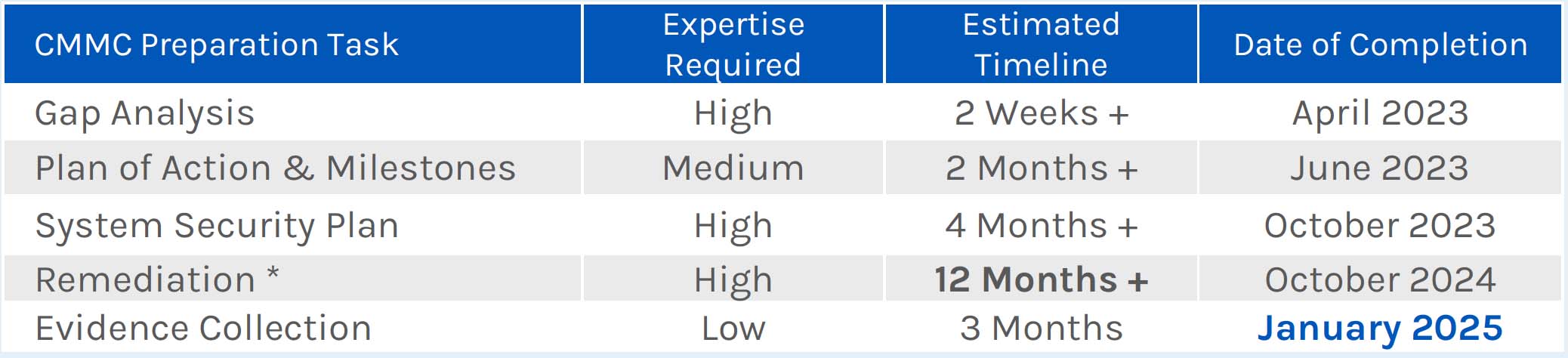
So with that said, one of the things I really want to try to get across is definitely start your preparation. It takes time. It's a change in your business. There's several things that you'll need to get done in order to get to a point of full compliance, starting with a gap analysis, understanding where you stand today and then creating a Plan of Action and Milestones (POA&M) for remediation.
The System Security Plan (SSP), and we'll get into it in a little bit more detail later. But it's got to be really well thought out and have enough detail in it for the assessor to be able to rely on it.
And then the remediation often takes a long time. And this is really the 80/20 rule. There's a lot of things that are really not that hard to do. And then there's that 20%, that's very, very difficult. And I'll get into some some examples later of some things that we've seen with our customers.
And then the last part of it is evidence collection, making sure that you have all your ducks in a row, when the see C3PAO comes in.
But you're looking at approximately 20 to 24 months for organizations to do it themselves. If you have a third-party provider, you can get it done a little bit quicker, but there's still going to be things that you'll find that really are things that slow you down, especially in the remediation phase. So anyway, this is just really important. You're looking at 2025, if you start today. And hopefully most of you have already started.
Five Barriers to CMMC Compliance:
So let's talk about some of the things we've seen. So we help lots of companies through CMMC compliance. And right now, there's not been any certifications. But many of our customers are either almost or fully ready for certification. But we've seen several things across the board, that just keep coming up time after time. And so that's what we're focusing on today.
- Understanding how CUI flows through an organization:
So things like understanding how CUI flows in your organization. Ultimately, that's going to determine the scope of CMMC. So if you understand where CUI flows, you have a really good understanding and documented CUI flows, then you can scope down CMMC efforts to a certain number of devices, facilities and people, that makes a difference in cost. But then the flip side of it is if you try to do your whole organization, for CMMC, it becomes unmanageable, and it takes that much longer. And so that's why CUI flow is so important understanding where that data flows. And that's what we're protecting is Controlled Unclassified Information. - Inadequate policies, procedures & compliance-related documentation: Another thing we see is inadequate governance documentation, things like policies, standards, and procedures, the System Security Plan (SSP), the Plan of Action and Milestones (POA&M). A Compliance Responsibility Matrix is how you divide out the responsibilities for compliance, specific to your service providers. You may have a security service provider, you may have an MSP and then also the organization itself. And that has to be well documented so that the C3PAO can attest in the right places.
- Limited security monitoring & incident response capabilities: Also, limited security monitoring and incident response capabilities is something else we see is an issue for a lot of organizations. They don't have a SIEM in place today, they don't really have an incident response capability.
- FIPS-Compliant vs. FIPS-Validated Encryption:
Then the other thing, this is something that's huge, is FIPS-compliant versus FIPS-validated encryption. This is something that can really cause delays in your certification process and compliance. A lot of people read the FIPS requirements within NIST SP 800-171 and they don't see the nuance of FIPS-validated encryption versus FIPS-compliant. And so a lot of products, they will say that they're FIPS-compliant, but that does not mean that they're FIPS-validated, which means a third party is actually testing to make sure that it meets the standards. And we'll talk about that in more detail. - FedRAMP-Equivalent Cloud Services:
And then the the last thing is FedRAMP equivalency for cloud security services. And there's talking about MSPs as well possibly falling into this realm. Though I doubt that will happen. But FedRAMP is a lot more rigorous than CMMC even. And so a lot of cloud service providers have not gone down this path and that also means Software-as-a-Service (SaaS. That means applications that you might have in the cloud. So it’s very important. And now the requirement is FedRAMP equivalency. So they don't have to be FedRAMP authorized. We'll discuss this in more detail a little bit later, but if they say they're FedRAMP equivalent, then you have to have a way of demonstrating that. And so that's where the rub comes in for that. So we'll get into these in more detail.
1. Understanding CUI Flow:
So let's talk about the CUI flow, and how you know how to do a CUI flow analysis. So, a CUI flow analysis is really looking at business processes within your organization, determining what business functions actually support your DoD contracts. From there, you can identify the processes within each one of those business functions. And then you can determine whether that process and what parts of that process actually handle CUI.
You can then from there map the flow of CUI through each business process. And that includes where people touch it, where it goes to different facilities, applications, and even networks and systems. And then you're going to categorize the systems and determine your CMMC scope. Whether it's a CUI asset or security protection asset or a contract or risk manage the asset. And we'll do another webinar on scoping and how scoping works. It's a little complicated, but there is a scoping guide that DOD has published on the CMMC website.
Business functions that handle CUI:
So let's talk about how this might work. So I've got a very simple organization here. It's got three business functions within an organization. We just have people, which is the human resources, function, production, and business development. And so what we've determined is that, because it's a manufacturing company that has Controlled Unclassified Information (CUI) that's shared by DOD, that the business development function, and then also the production function within the company would have access to that CUI. And this is over simplistic, by the way, but I'm just trying to get the point across here.
So this is just an example of a manufacturing process that starts with business development and all the way to the point where you're shipping to your customer. And from there, we're mapping out the applications and where CUI actually flows. And so you may find that some of these applications don't have any CUI in them. And then other applications, they do have CUI. So one good example of one that might not have CUI or any Controlled Unclassified Information is ShipWorks, which is the last one over in the right corner. In this case, you would be able to determine which applications, which networks those applications sit on, which facilities that data sits in, and don't forget about paper copies. So this understanding of how CUI flows is super important.
So I've gone through this very quickly, but if you have additional questions, we're happy to jump on a call and explain this in further detail on any of these things.
2. Inadequate Documentation:
Inadequate documentation is another huge area. So let's talk about what's required for CMMC Certification at a minimum. The first thing that an assessor is going to ask for is that System Security Plan (SSP). And if you don't know what a System Security Plan is, there is an SSP Template on the NIST SP 800-171 Rev 2 website. And we'll have a screenshot later, but that's something you're gonna have to have.
As part of that you'll have to have architecture and CUI flow diagrams. You've got to demonstrate where the CUI flows. The policies and procedures that are used have to be in place to address all of the 110 requirements of NIST SP 800-171.
Another thing that's required within the NIST security configuration standards specifically for technologies, you may want to have technology standards in place for Windows and Linux and other applications. So these are configurations of those. You may also want to have technology standards for things like access control and encryption and minimum levels that your organization is going to accept.
Another thing, and this is huge, is something in early assessments that CMMC is doing at this point is the incident response plan and capability for the organization. This is turning out to be one of those areas that there's a lot of focus on right now. So incident response is something that you're going to have to focus on the compliance responsibility matrix I spoke about a little bit earlier in the presentation. It’s a spreadsheet that lays out each one of the requirements, and then who's responsible for each part of it. And so you may have shared responsibility for some controls with a service provider that provides all of the compliance for another one. So that's important because the C3PAO is going to need to know what to look at and where the controls are being applied.
Another thing that's very important is an asset inventory. So it's an inventory of people in your organization. It's an inventory of the software and computer systems and even PCs as well. And the reason why you need that inventory is because you have to assign a CMMC scope to each one of those assets.
And then lastly, there's evidence of compliance or artifacts that you'll need to collect. So these are documents that are required. And I can tell you, we've reviewed many System Security Plans (SSPs) and policies and standards, and oftentimes,we see that there's a lot of policies in one document, and nobody really knows how to use it within an organization. Oftentimes, IT policies are jumbled with user-specific policies to try to make it as clear as possible. That's something that's going to help your organization and then it'll also help with your compliance efforts.
SYSTEM SECURITY PLAN:
So when we talk about the System Security Plan (SSP), there's three sections. The first one is the System Identification, which includes things like roles and responsibilities, who's responsible for the systems, who's responsible for CUI and information, and things like that.
The second section is going to be a narrative of the system environment. And this narrative basically lays out the architecture of the system, and the controls that are applied, as well as the CUI flows and things like that about the organization.
And then section three is all 110 requirements. And then there's a narrative or response that needs to be put in place that says how your organization actually meets those requirements.
We had a situation recently where we reviewed a System Security Plan (SSP) for a customer and what we found was that they had a couple of sentences underneath each one of the requirements that said they used Active Directory for access control and their IT administrator grants access based on e-mails received from company managers. And that's pretty much what it said. But that's not enough information. So a good rule of thumb as you're going through Section 3 of that System Security Plan (SSP) is to answer all six of the assessment objectives. Everything that you put in your response for how you're compliant with that one control.
In addition to that, you're also going to want to put supporting documents, compliance artifacts, and any policies and standards that apply. And so you can see at the bottom on the right side of our response here for Acme Inc. is that we listed out all three of those areas. And that way, the C3PAO can go ahead and easily reference those policies and standards. If you have the artifacts already in place, it's going to make it a lot easier to get through your certification assessment. Because your C3PAO or your certified assessor may say, “Well, hey, can you just show me this?” But oftentimes, they'll rely on your own artifacts. So they'll do spot checks to make sure that your artifacts are accurate. If you're able to gather all those artifacts, your assessment will cost less.
SECURITY Policies and Procedures:
So let's talk about security policies and procedures. So there's a difference between security policies and procedures. And we see situations oftentimes where they're jumbled together. If they're jumbled together, that's an issue. A security policy is a statement by organizational management on how an organization will do something. And it's very similar to a law like you're not allowed to steal, for example. Well, in this case, a policy might be that as far as an encryption policy, sensitive information must be protected from unauthorized disclosure when sent across untrusted networks. That would be would be the way that a policy statement would look for encryption. And then you might see the encryption standard for additional information. And so that's how we protect information as it goes across untrusted networks as it's encrypted.
When it comes to a procedure, a procedure is a step by step on how something is done. So the procedure that's on the right side of the screen here is actually a workflow for the procedure and not the procedure itself. But you can see there's steps in the process. So it's just like baking a cake, where you're going to add the ingredients to the cake, then you're going to put the cake in the oven, and then it's step by step, one after the other. That's what a procedure is.
Governance Framework:
So when we look at governance, that includes the policies, standards, procedures, and any supporting documents. So we talked about what a policy is. A standard is basically a further definition of how to meet a policy. So they could all kind of work together. And then the procedure would be how a policy is met. So this is the step-by-step instructions on how to meet the policy requirement using the standard.
And then a supporting document would be something that is used to support the procedure. And I'll just give you an example. A visitor sign-in sheet is a good example of a supporting document. So there's a procedure for allowing visitors into a facility and a supporting document in this case would be the visitor sign-in sheet.
NIST CMMC RESOURCES:
So I talked about this earlier, but there's some great resources that NIST provides. It's on the NIST SP 800-171 Revision 2 website. And you can see, there's the Plan of Action and Milestones (POA&M) template, there's a System Security Plan (SSP) template. You can also look at the Assessment Guidance, which is NIST SP 800-171A. And that's what you're going to use in crafting a response in your SSP.
3. Security Monitoring & Incident Response
So security monitoring and incident response is another thing we see that is consistently not in place. So we talked about security monitoring. This is a Security Information and Event Management (SIEM) system that records security logs from different locations within the organization. Different systems within organization are all aggregated into a single location. And then alerts will be triggered if there's a security event if there's an Indicator of Compromise (IOC). And so, it’s very important to have these systems in place, because it gives you visibility into what's happening from a security perspective on a real-time basis.
And if you look at the screen here, this is just the US Screen of one of our the SIEMs that we use. And so you can see that there's relevant information as far as traffic, as far as attacks, that security professionals can use to can determine if an attack is actually happening. And let me just give you an example of how that might work. So one of the visualizations that you might have is a visualization that shows failed Logon Attempts. And when you start seeing a spike inb failed Logon Attempts, even though it may not be tripping an alert, that is an Indicator of Compromise (IOC) potentially. And that's what a security analyst would use to find those types of things.
And this is important, because this is a requirement for NIST SP 800-171. Having that visibility is an element of a basic security program. So oftentimes, you will find something from a SIEM or from security monitoring, where there's an attack or there's something that's happening. And so there needs to be a response to those types of things. And so just as a couple of things that that are going to need to be in place.
One, you've got to have an incident response plan. And it's got to be well thought out, it can't be a two-page document. Typically, you can't really address this in two pages. It's got to have roles and responsibilities. These are different from corporate roles and responsibilities. It's just like a Business Continuity plan in that way. There should be a pre-assembled tool set. So if you have a system intrusion, what tools are you going to use? If you have a malware outbreak, what tools are you going to use? And then pre-determined legal and law enforcement contacts as well. So it's always important to know people that are that are within law enforcement. In the case of cyber, it's somebody from the FBI or the Secret Service that's going to handle law enforcement in most cyber cases. But it's good to have those contacts already in place, so that you can make phone calls and get people involved as quickly as possible. And then also your attorney and that kind of thing.
And then lastly, each incident response plan should have procedures for common types of incidents. So some of the examples of common types of incidents would be things like a malware outbreak or system intrusion, as I mentioned earlier, or lost and stolen laptop, escalation of privileges, or abuse of privileges within your organization. So, oftentimes we've done incident response for companies that have had system administrators that were looking at executive e-mail. And so that was suspected. And we found that was actually happening. And so those are the types of common incidents.
And then the last thing is you've got to do periodic incident response training exercises. So training is super important. One of the first things the C3PAO is going to do is look for evidence that training exercises have happened. And so, in that case, it's usually scenario-based exercises. And so you'd have a scenario or a situation where you have a malware outbreak. And so your response might be a tabletop exercise as an organization. So there should be things that come out of it that will help improve your actual procedure as well. So there should be lessons learned. So that's one thing that a C3PAO is going to be looking for is evidence that each exercise has happened that should be collected as an artifact. So you should have a report of who attended. What were the lessons learned? What were the action items after that for the incident response exercise.
And to give you a little bit of a color on this, we do these incident response exercises for customers. We had a situation where we had one scheduled for 10 o'clock in the morning on a Tuesday. And we jumped on with the customer and found out there was actually an incident happening. It was different than the exercise we were planning on doing, but we went through the whole incident response, in lieu of that exercise at that point. In that case, I think it was a stolen laptop, if I'm not mistaken. And so these things happen. The larger the organization, the more frequently you'll see incidents of one sort or another.
Now, bear in mind, this is something that's really important, DFARS 252.204-7012 requires notification to DOD, if there is a security incident where you suspect the breach of Controlled Unclassified Information (CUI), you've got to have a method of contacting DoD as well. So that's something that's also very, very important.
4. FIPS 140 Validated Encryption:
This is a huge issue that we see. So the net of it is every system that handles CUI or encrypts CUI in any way. That could be backups, that could be wireless systems, that could be your VPNs, workstations where you have storage encryption. Those devices have to be FIPS-validated. And the only way to figure out if it's FIPS validated is to determine what crypto module is actually being used for the encryption and then search the NIST website to see if it's actually gone through the validation process. If it hasn't gone through the validation process, this will cause a failure for CMMC. So that's something that's really important to know. And oftentimes, it's a surprise.
And so, just as an example, we've had customers using an encryption technology that was part of our remote management system. And the modules were not FIPS-validated, they said it was FIPS -ompliant. And so because of that, they're in a situation where that tool that's used to support the entire enterprise is not going to be able to be used unless the vendor actually gets those FIPS modules validated. Because it does touch CUI. So this is one of those things that's definitely a gotcha.
5. FedRAMP Equivalent Cloud Services:
So FedRAMP is one of those standards that DOD came out with somewhere in the neighborhood of 10-12 years ago. What they found was that cloud service providers that handled government information didn't have the necessary security controls in place. And so they required cloud service providers to be compliant with NIST SP 800-53, which has a lot more requirements than NIST SP 800-171, which was derived from NIST SP 800-53.
So it's a process to get through FedRAMP certification than FedRAMP authorization. And so a lot of cloud service providers and SaaS have not gone through that. We had a customer that has a software application that is absolutely critical to their business. And we had a conversation with their SaaS provider and basically told them, “Our customer is subject to CMMC and has Controlled Unclassified information (CUI) stored in your cloud service, which requires your application to be FedRAMP authorized.” And we were told two years ago, “Yeah, we're moving towards that. We should get there in probably about a year or so. We're looking at getting our FedRAMP authorization.”
Well, fast forward to June of last year and we were finally able to get back in touch with them after multiple attempts and they basically told us that they had decided to focus on other business priorities, and they're not going towards FedRAMP. So that put our customer in a very, very difficult situation. And we're in a situation right now where we're trying to use the same business application, but move the CUI to another place and still not break their business processes.
So bear in mind, this is something that is if you miscalculate this, it can have a huge impact on your business. And so, you know, FedRAMP is huge.
Now, here's the thing, the requirement is FedRAMP equivalent. But you have to prove that the cloud service provider has all the controls in place for FedRAMP. And we've seen one situation at this point where there's actually been FedRAMP equivalency. So for the most part, it’s gonna save a lot of headaches if they're just FedRAMP-authorized.
And so there are quite a few cloud service providers that are in the process right now. There's 87 in process and 296 that have been authorized. And bear in mind, it's over a 10-year period, so a lot of the cloud service providers and SaaS providers are understanding this is going to be a requirement for CMMC. And they're going to lose customers that are defense contractors, if they don't go through the process. So they're going through it right now. So that's something to definitely check. And make sure you get things in writing as well. Very important.
So with that, I just want to go ahead and open it up to some questions.
Questions?
If you have any additional CMMC compliance questions that you need answered, please consider booking a free, one-on-one consultation with an InfoDefense CMMC compliance expert.
INFODEFENSE RESOURCES:
Here are useful InfoDefense materials from the 5 Steps to CMMC Compliance Webinar:
LINKS:
These are helpful links to the online resources referenced during the webinar:
WEBINAR Q&A:
Do we have a timeframe for when we expect CMMC rules to be finalized?
Let me just tell you what the ODS told us. DOD said that they were planning on finalizing the CMMC rules this month, March of 2023, but it's been delayed at this point.
We're looking at my guess is June timeframe, because DOD has got to finish their thing. And I think that's pretty close from what I understand.
And then it's got to go to the Office of Management and Budget (OMB) and they have 90 days. And then it will be more than likely a Notice of Proposed Rulemaking.
So what I'm understanding, is they're not going to do the Interim Final Rule right away. And what that does is it basically provides for feedback over a period of time and adjudication of that feedback before the final rule is completed.
And so look for rule making sometime this summer. And don't hold me to it. This is all based on DoD timeframes.
If we don't achieve CMMC compliance by that date, what does that mean for our business?
So you will not be eligible for contracts. If it's in the contract as a requirement, you will not be eligible for that contract. And so this is one of the reasons why CMMC is so important. When it comes down to it, whether you achieve CMMC certification or not, it will determine whether you can do business with the Department of Defense or specifically respond to a contract that has a CMMC requirement. And so, if 50% of your business is DOD, you should be on top of this right now.
If a small part of your business is DOD business, you're really faced with a decision. There's gonna be a lot of companies that decide not to pursue CMMC, because it is kind of onerous.
So if you decide to go down this path,
So if you decide to go down this path,
there's an opportunity that you're gonna have less competition for those contracts, so you can increase your business with DOD.
The other option is you could decide, well, "Hey, we don't want to do any DoD business going forward," and then just decide to drop out. I don't want to encourage that. But that is definitely a business decision companies do make sometimes.
What do we do if we haven't submitted our SPRS score yet?
If you have not submitted your SPRS score, it has been a requirement for two years now. Get your SPRS score done as quickly as possible. We have a free assessment tool for NIST SP 800-171 that you can use to calculate your SPRS score. So it is important to get that SPRS score done.
How long does it take for CMMC Implementation?
That all depends. We know companies that have been working on CMMC implementation for three years plus. But we also have a CyberSecure 360 service that we provide to help DoD contractors achieve CMMC compliance much quicker, sometimes in as little as six months, depending on the size of the company. But we recommend that companies on average plan to take 18 months to two years. because trying to complete the certification process too quickly can cause what we call organizational whiplash.
